Additional Steps
There are some additional steps that are not needed but are strongly recommended in such a deployment. They will make it harder to bypass the filtering or greatly minimize the administrative burden in our network.
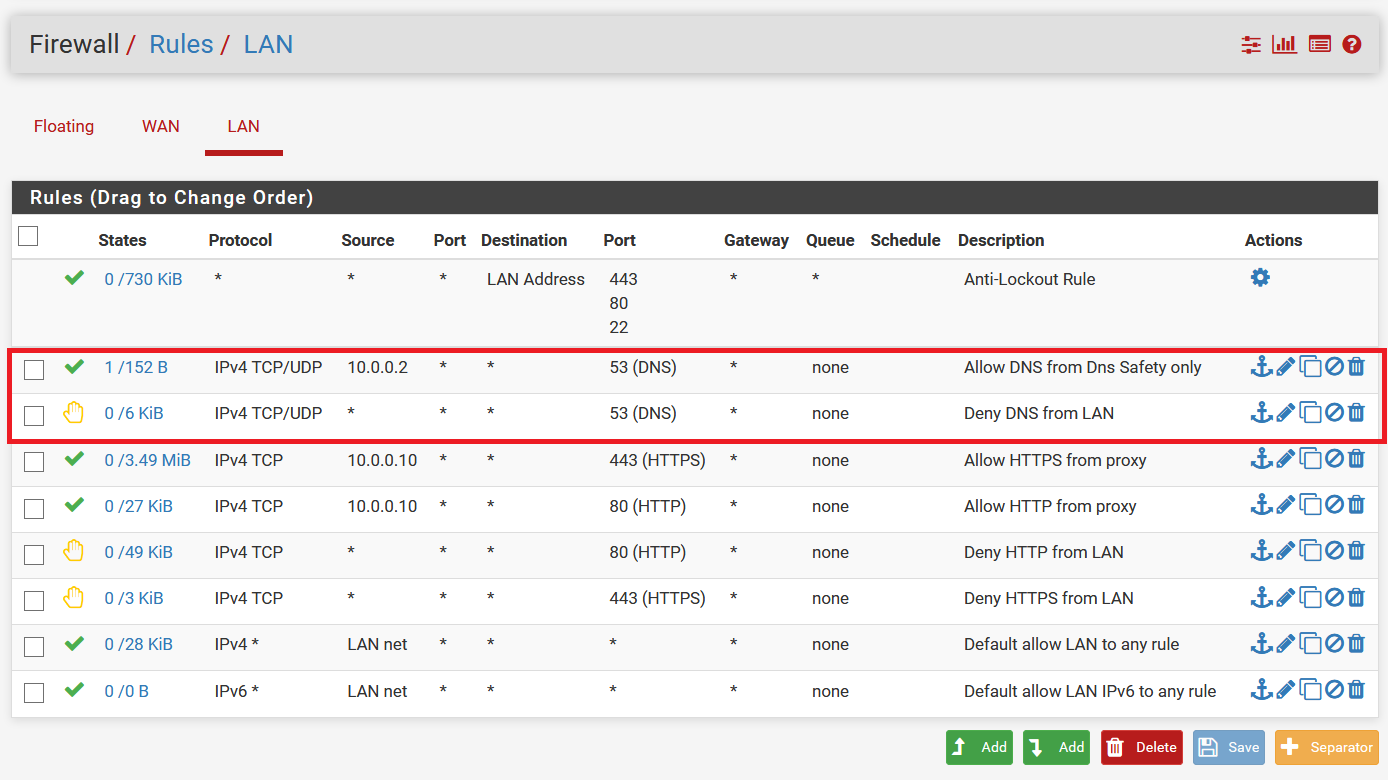
Restrict DNS Requests
To prevent circumventing of DNS requests be sure to only allow outgoing connections to port 53 only from DNS Safety host like indicated on the following screenshot.
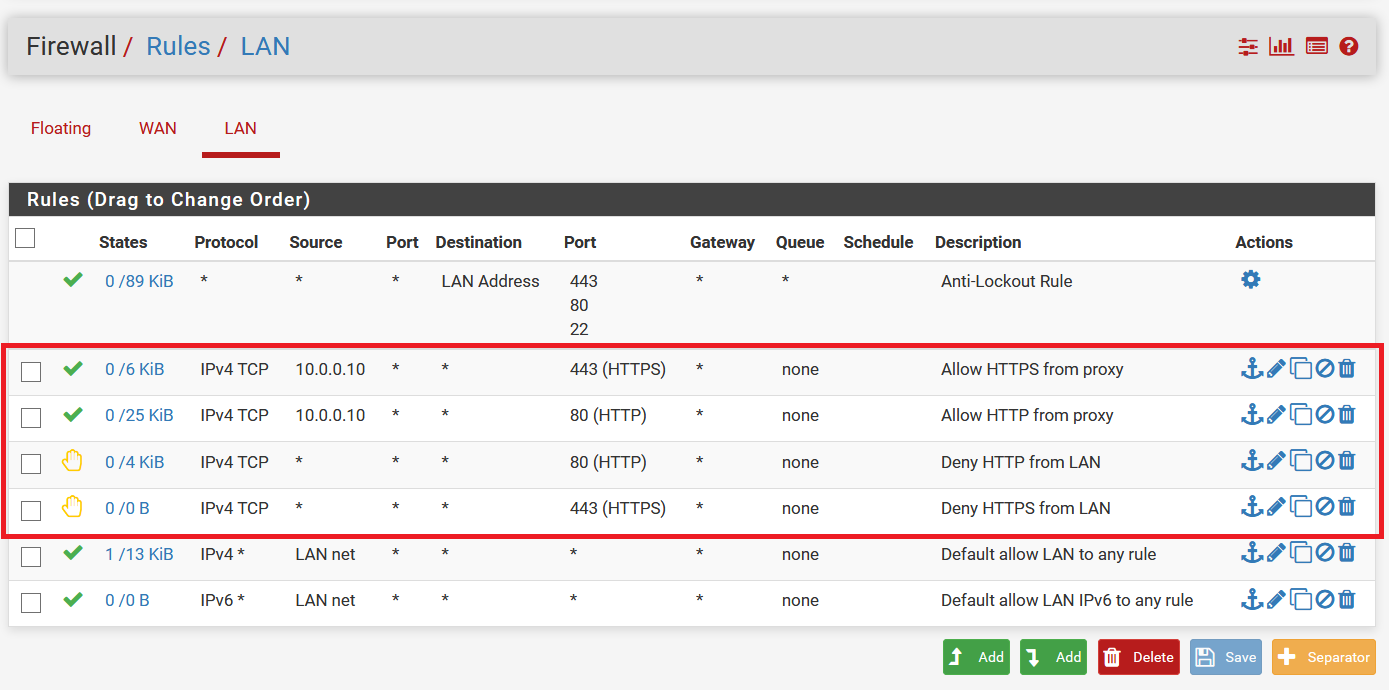
Restrict Web Access
If you would like to force the internal clients within your LAN to always use the proxy to connect to the Internet, it is advisable to block outgoing access for TCP protocol to ports 80 and 443 on your network unless this access is done from your proxy (by IP 10.0.0.10). This will allow outgoing HTTP/HTTPS requests to come from proxy only. By doing this you ensure the HTTP/HTTPS traffic went through your proxy and was filtered as desired.
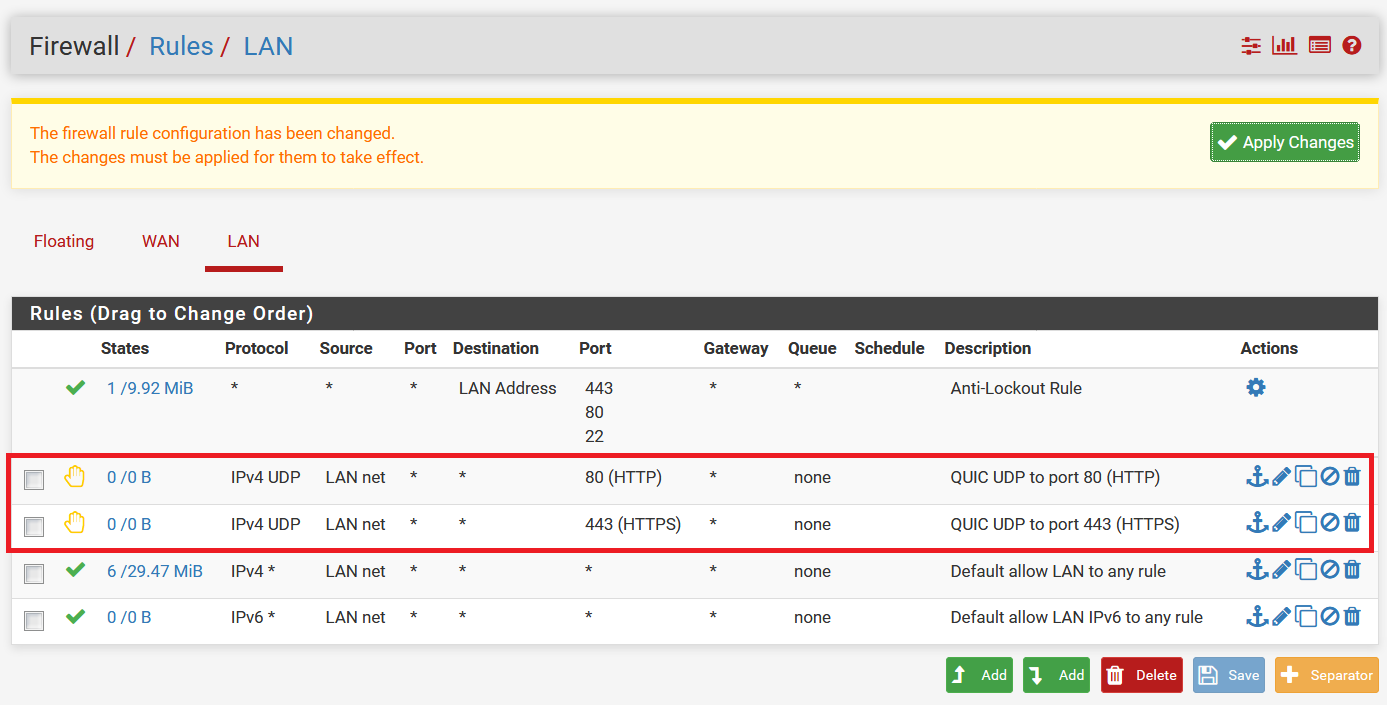
Block QUIC Protocol
Google added an alternative protocol that can be used to access Google services (including YouTube). It is called QUIC. It is advisable to block QUIC protocol on your pfSense firewall, otherwise Chrome will be able to bypass web filtering.
To block the QUIC protocol, add REJECT rules for UDP protocol on outgoing port 80 and port 443 as shown on the following screenshot.